
Introduction:
For many of us, our mobile phone is more than just a device; it’s an extension of who we are. It holds our closest friendships in messages, our fondest memories in photo albums, our finances in banking apps, and our entire lives in a digital tapestry of data. We carry it everywhere, and in doing so, we operate with a quiet, unshakeable faith in its security. We believe that because it’s always with us, it’s always safe. We trust the slick technology, the biometric authentication, and the glowing logo on the back to protect us.
But this belief is, in many ways, a myth. The modern smartphone, with all its power and convenience, is a treasure trove of sensitive information, and it is a prime target for those who seek to exploit it. The illusion of a personal digital fortress is comforting, but in reality, it’s a home with many doors and windows, and a surprising number of them are left unlocked by default. Hackers, data brokers, and scammers don’t need to be criminal masterminds; they just need one small crack in the armor to slip through.
The purpose of this guide is not to incite fear, but to foster awareness and empower you. We’ll move beyond the intimidating technical jargon and break down the essential security settings into simple, actionable steps. Think of it as a friendly conversation, a walkthrough of your digital home. We will identify the weak points and, together, we will reinforce them. By the end of our journey, you won’t just be a mobile phone owner; you will be the vigilant guardian of your digital life.
Table of Contents
The Foundation – The Lock Screen and the Golden Rules
Before we get into the more complex layers of security, let’s start with the absolute basics. Your lock screen is the front door to your digital life. It is the single most important barrier between a stranger and your sensitive data. Without a secure lock screen, every other setting we discuss is almost meaningless.
Your First Line of Defense: The Lock Screen
We’ve all been there: fumbling for our phone in a hurry, eager to check a notification, and just wanting to get in. For the sake of convenience, many of us choose a simple 4-digit PIN, a swipe pattern, or something obvious. It’s quick, it’s easy. But is it safe?
Passcodes vs. Biometrics (Face ID/Touch ID): While biometrics like Face ID and Touch ID (or their Android equivalents) feel like something out of a sci-fi movie, they are, for the most part, incredibly secure and convenient. They make it nearly impossible for a thief or a curious bystander to get into your device. However, biometrics should always be backed up by a strong passcode. Why? Because biometrics can sometimes fail, and more importantly, in some legal situations, you can be compelled to unlock your phone with your face or fingerprint, but not necessarily your passcode. This is where the strength of your alphanumeric code comes in.
The Power of a Strong Passcode: A 4-digit PIN has only 10,000 possible combinations. A savvy criminal can crack it in a matter of minutes, especially if they’ve seen you enter it. A simple 6-digit PIN is better, but still relatively weak. The real power lies in a custom alphanumeric passcode. This can be a mix of letters, numbers, and symbols. It’s a pain to type, yes, but think of it as a small price to pay for a fortress-level of security. Go to your settings now and change your passcode. Use a phrase you can remember, maybe something that doesn’t make sense to anyone but you, and use a mix of capital and lowercase letters.
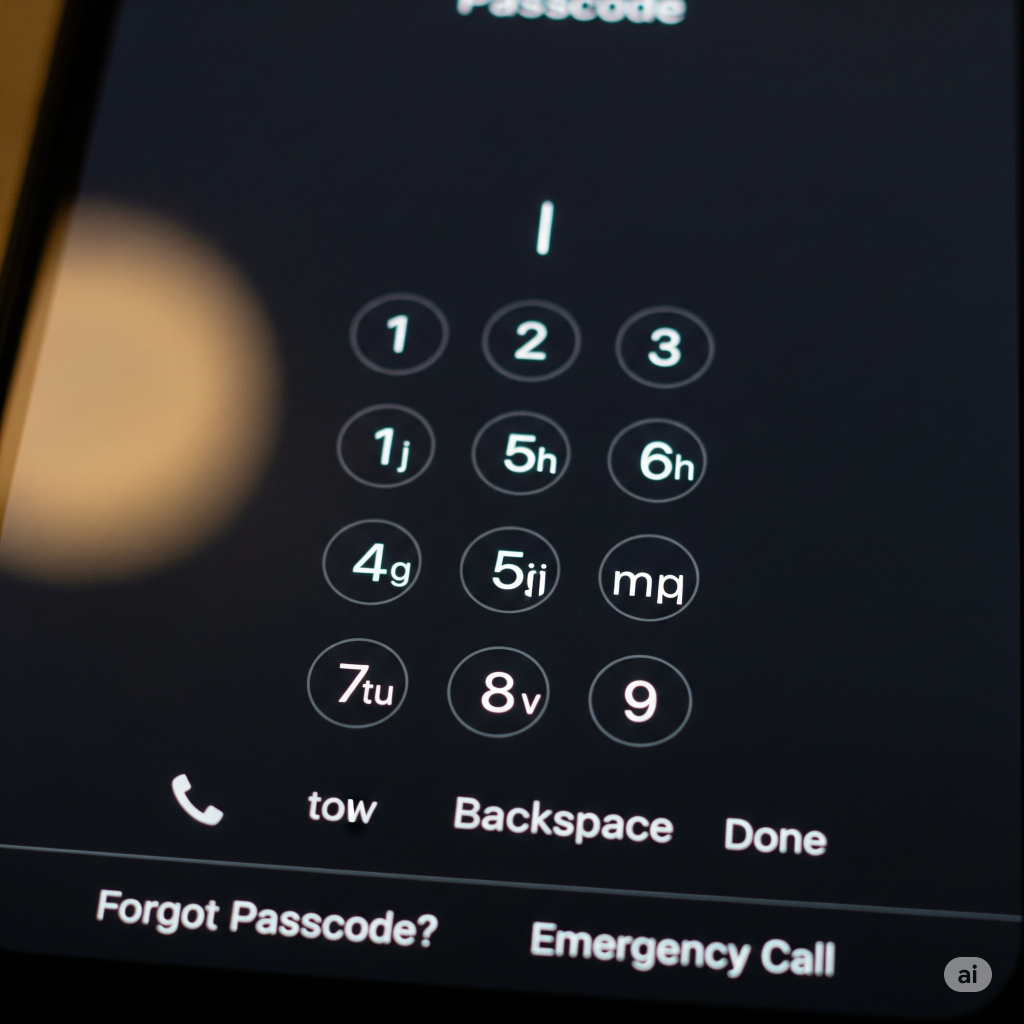
The “Auto-Lock” Setting: This is perhaps the most overlooked setting on your device. It controls how quickly your phone locks after you stop using it. By default, it’s often set to a few minutes. Think about it: you put your phone down on a table at a coffee shop, get up to grab a napkin, and in that moment, your phone is still unlocked and vulnerable. Change this setting to the shortest possible time, ideally 30 seconds. It might feel a bit annoying at first, but it’s a tiny inconvenience that offers monumental protection.
The Stolen Device Protection (iPhone) / Find My Device (Android): Your Digital Panic Button: This feature is not just for finding a lost phone; it’s your emergency response system. If your phone is lost or stolen, these features allow you to remotely locate it, lock it, display a message with your contact information, or, in a worst-case scenario, erase all its data to prevent a thief from accessing it. This should be enabled right now if it isn’t already. It’s the ultimate last resort that gives you back a crucial measure of control.
The Golden Rules for Every User
Beyond the lock screen, there are three habits that form the bedrock of mobile security. These aren’t settings to toggle; they are mindsets to adopt.
Rule #1: The Update Imperative. We’ve all seen the pop-up notification: “iOS/Android Update Available.” And we’ve all hit “Update Later” because we’re busy. But here’s the thing: those updates aren’t just for new emojis and features. They are the digital equivalent of an emergency repair crew. They contain critical security patches that fix newly discovered vulnerabilities. When a company like Apple or Google releases a security update, it’s because a hole has been found in the software that a hacker could exploit. By delaying the update, you’re essentially leaving your front door unlocked with a giant sign that says, “I know my lock is broken, but I’ll get to it later.” Make it a habit to install updates as soon as they become available.
Rule #2: The App Store Sanctity. The Apple App Store and Google Play Store are not perfect, but they are the safest places to download applications. They act as gatekeepers, scanning apps for malware and malicious code. When you “sideload” an app (download it from a third-party website) or “jailbreak” an iPhone or “root” an Android device to install unapproved software, you’re bypassing this crucial security check. It’s like inviting a stranger off the street and giving them a key to your house without knowing their intentions. These unvetted apps can contain anything from hidden trackers to dangerous malware that can steal your personal data, bank information, or even hold your phone hostage with ransomware. Stick to the official app stores. It’s a simple, non-negotiable rule.
Rule #3: The Backup Habit. What’s the worst that could happen? Your phone gets dropped, stolen, or corrupted. All your photos, contacts, and personal data are gone in an instant. This “what if” scenario is not a matter of if, but when. Backing up your phone to the cloud (iCloud, Google Drive) or a physical computer is not a sign of paranoia; it’s a testament to good planning. It ensures that even if you lose your digital fortress, you still have a copy of the treasure it held. Schedule automatic backups. It’s a set-it-and-forget-it task that will save you from a digital heartbreak in the future.
The Silent Threats – App Permissions and Data Privacy
You’ve secured your front door with a strong lock screen and adopted the foundational security habits. But what about the guests you’ve already invited in? The apps on your phone are like visitors in your digital home. Some are trusted friends, while others might be quietly rummaging through your personal belongings. The biggest threat to your privacy often comes not from a remote hacker, but from the apps you willingly downloaded.
The Curious Case of the Microphone and Camera
When you first install an app, it often asks for a long list of permissions: access to your camera, microphone, contacts, photos, and location. It’s so routine that many of us just tap “Allow” without a second thought. But what are you really allowing?
- The Reality of App Permissions: Granting a social media app access to your camera seems logical. But why would a simple flashlight app need access to your microphone and contacts? The permissions you grant are a blueprint of your privacy vulnerabilities. An app with microphone access could be listening to your conversations (even in the background). An app with camera access could be taking photos without your knowledge. An app with contacts access could be siphoning your entire network of friends, family, and colleagues for data.
- The App Privacy Report (iPhone) / Privacy Dashboard (Android): The “Aha!” Moment: Both iOS and Android have a brilliant feature that pulls back the curtain on app behavior. You can find it in your phone’s privacy settings. It’s a report that shows you exactly which apps have accessed your camera, microphone, location, and other sensitive data, and when they did it. Seeing the visual representation of a weather app accessing your location 20 times a day or a random game accessing your photos can be a startling “aha!” moment. It’s the moment you realize how much data you’ve been giving away without even knowing it.
- A Humanized Walkthrough: Go into your settings now and review your permissions. It’s a simple, but powerful exercise. For each app, ask yourself:
- Does this app absolutely need this permission to function? (A mapping app needs location; a photo editor needs photos).Is there a more restrictive setting I can use? (Instead of “Always” accessing location, can I choose “While Using the App”?).
- If the app’s need for the permission seems questionable, can I simply deny it?
Taking five minutes to manually review these settings is one of the most effective ways to reclaim your privacy. It’s about being intentional with your data, not just giving it away for the sake of convenience.
The Invisible Trackers and Data Brokers
The digital economy is built on data. Companies track your behavior online and on your phone to build a profile of you. This profile is then sold to advertisers who use it to serve you highly targeted ads. You see an ad for shoes just after searching for them, and you wonder, “How did they know?” It’s not magic; it’s an invisible web of trackers.
- App Tracking Transparency (iPhone): Apple’s “Ask App Not to Track” feature was a groundbreaking moment for mobile privacy. It puts the control squarely in your hands. When an app wants to track your activity across other companies’ apps and websites for advertising, a pop-up appears asking for your permission. Tapping “Ask App Not to Track” blocks the app from collecting this data. It’s a simple toggle, but it puts a significant roadblock between your digital footprint and the companies that want to monetize it. Don’t be shy; always choose the “Ask App Not to Track” option.
- The Location Dilemma: GPS data is one of the most valuable pieces of information a company can collect. It can track your home, your workplace, your routine, and your habits. When an app asks for your location, you often have a few options: “Always,” “While Using,” “Ask Next Time,” or “Never.”
- Always: This allows the app to track your location 24/7, even when it’s not open. This is almost never necessary.While Using: This is a good balance for apps like maps or ride-sharing.Ask Next Time: This is the most secure option for many apps. It forces the app to request permission every time it needs your location, making you consciously aware of when you are giving that data away.
- Never: The safest option if an app has no legitimate reason to know where you are.
Making a conscious choice about your location data is a powerful step towards protecting your privacy.
The Connected World – Wi-Fi, Bluetooth, and Phishing
Your phone is a communication hub, constantly sending and receiving data. While this connectivity is what makes it so powerful, it also introduces a new set of vulnerabilities. Just like a house with an open window, your phone’s connections can be a pathway for a digital intruder.
Public Wi-Fi: The Digital Coffee Shop
We’ve all done it: logged onto the “Free Wi-Fi” at a coffee shop, airport, or hotel. It feels like a small win, a way to save on data. But what you might not know is that these networks are often unencrypted and highly vulnerable. A skilled attacker can set up a fake network with a similar name (“Free_Starbucks_Wi-Fi”) and when you connect, they can monitor everything you do: your logins, your passwords, your banking information. This is called a “man-in-the-middle” attack, and it’s shockingly easy to execute.
- The Solution: The VPN. A Virtual Private Network (VPN) is your personal, encrypted tunnel. When you use a VPN, all of your phone’s traffic is routed through a secure server. This makes your data unreadable to anyone on the same public Wi-Fi network. Think of it as putting your digital information into a locked box before sending it across the public network. A quality, trusted VPN is a must-have if you frequently use public Wi-Fi.

Bluetooth: A Silent Pathway
Your phone’s Bluetooth connection is incredibly convenient for pairing with headphones, speakers, and your car. But keeping it on all the time, even when not in use, is a security risk. A nearby attacker could use an always-on Bluetooth connection to find your device and, in some cases, exploit vulnerabilities in your phone’s software to gain access. The best practice here is simple: turn off Bluetooth when you’re not actively using it.
Phishing, Smishing, and Vishing
The most common security threats don’t rely on technical exploits; they rely on human nature. Phishing, smishing, and vishing are all forms of social engineering, where an attacker tricks you into giving away your sensitive information.
- Phishing: This is the deceptive email. It might look like it’s from your bank, from Amazon, or from a social media platform, but it’s a fake. It’s designed to create a sense of urgency (“Your account has been compromised!”) or to tempt you with a reward (“You’ve won a prize!”), all with the goal of getting you to click a link and enter your login credentials on a fake website.
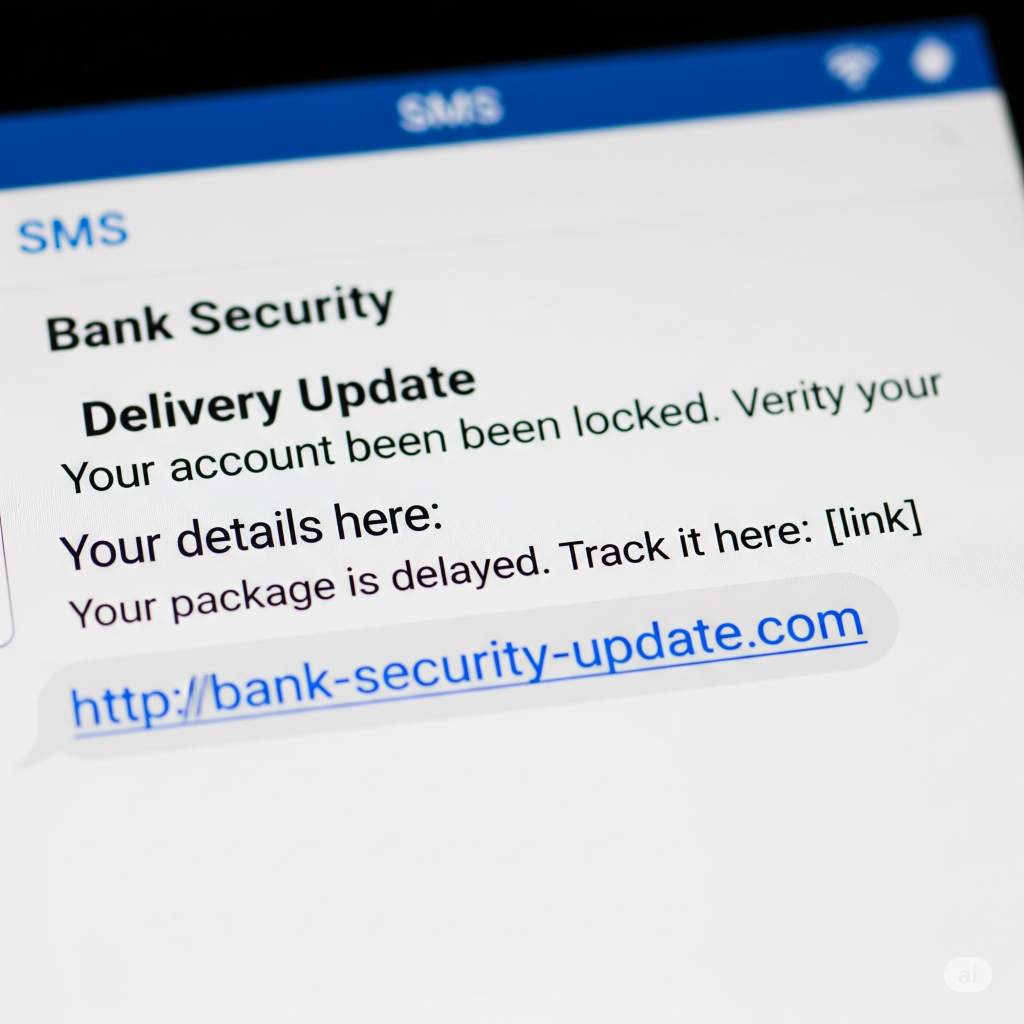
- Smishing: The same scam, but via text message (SMS). You might get a text claiming to be from a delivery company, a government agency, or even a friend, asking you to click a link to track a package or resolve an issue.
- Vishing: This is voice phishing, or a deceptive phone call. The caller might impersonate a tech support agent from Apple or Google, a bank representative, or a tax officer, claiming there is an issue with your account. They will then try to convince you to give them your personal information or grant them remote access to your device.
The defense against all three is to be a digital skeptic. Don’t click, don’t download, and don’t respond. If you receive a suspicious message or call, go to the official website of the company in question (by typing the address yourself) or call their official customer service number to verify the claim. The “hover and check” rule is your best friend: hover your finger over a link in an email or text to see the real URL before you click. If it doesn’t match the official company domain, it’s a scam.
The iPhone-Specific Deep Dive: Apple’s Walled Garden
Apple has built a reputation for its closed, “walled garden” approach to security, which often translates to a more secure user experience by default. However, there are still critical settings you must configure to maximize your protection.
- iCloud and Apple ID Security. Your Apple ID is the key to your entire digital life on an iPhone. If a hacker gets access to it, they can access your photos, messages, app purchases, and much more. This is where two-factor authentication (2FA) becomes non-negotiable.
- Two-Factor Authentication (2FA): 2FA is an essential safety net. It requires a second form of verification (like a code sent to a trusted device) in addition to your password. This means even if a hacker steals your password, they can’t log in without access to your physical phone or other trusted device. Set this up immediately if you haven’t already.
- Advanced Data Protection for iCloud: For those who want the ultimate privacy, this feature provides end-to-end encryption for the majority of your iCloud data. This means that your photos, notes, and backups are encrypted on your device before they are uploaded, and only you can decrypt them. Not even Apple can access this data, making it the highest level of security for your cloud backups.
- Safari and Mail Privacy. Apple’s built-in apps have privacy settings that are often overlooked.
- Mail Privacy Protection: This feature prevents email senders from using “tracking pixels” to collect information about you (e.g., when you opened an email, where you were, what links you clicked). It’s a simple toggle in your Mail settings that keeps this data from getting to marketers.
- iCloud Private Relay: Available with an iCloud+ subscription, this service hides your IP address and browsing activity in Safari. It’s not a full VPN (it only works in Safari and for certain app traffic), but it’s a fantastic privacy tool that prevents websites from building a profile of you based on your location and browsing habits.
The Android-Specific Deep Dive: The Open Frontier
Android’s open-source nature gives it incredible flexibility and power, but it also means security can vary across different manufacturers and models. Google has made great strides in centralizing security controls, but a proactive approach is still essential.
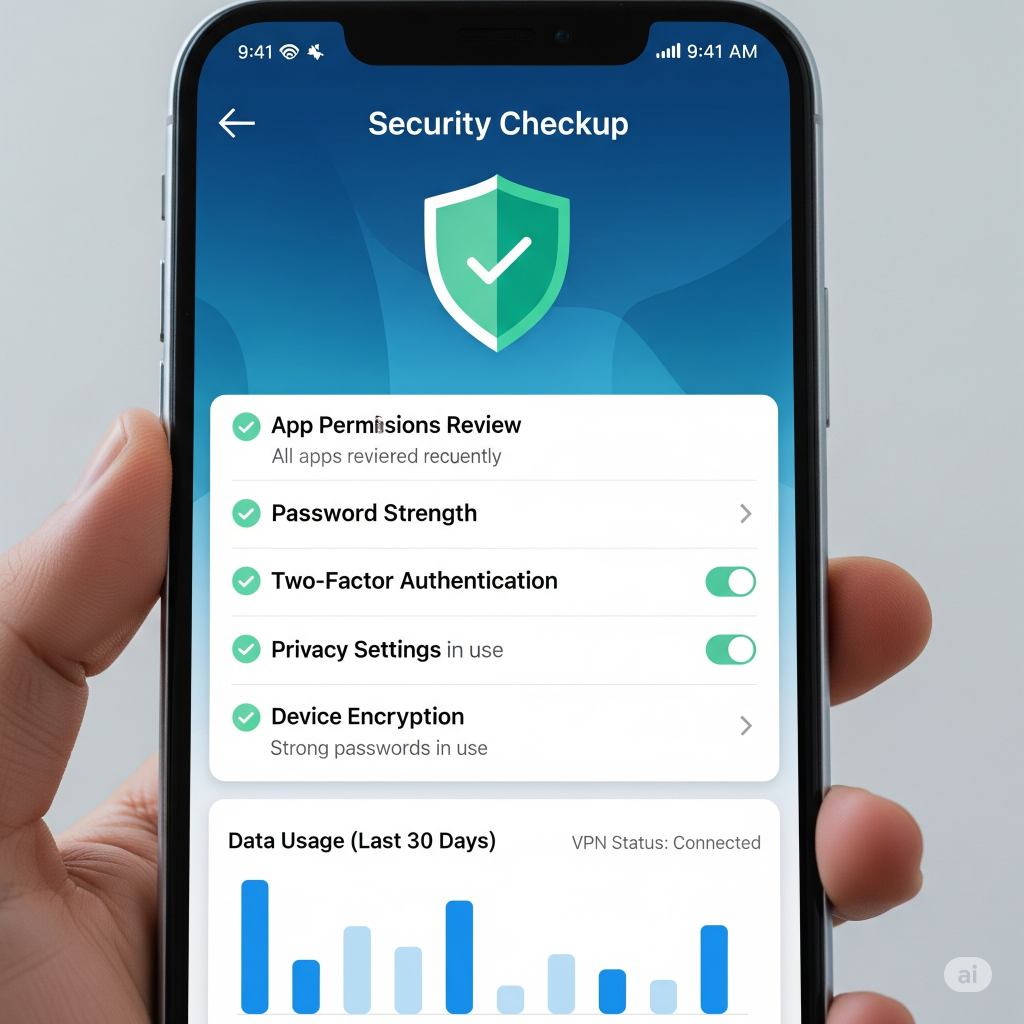
- The Google Account: Your Central Hub. Your Google Account is the heart of your Android device, and securing it is the most important step.
- Google’s Security Checkup: This is a personalized, comprehensive walkthrough of your account’s health. It will tell you if you have any compromised passwords, if you have 2FA enabled, and if any suspicious devices are logged into your account. Make it a habit to run this checkup every few months.Advanced Protection Program: For individuals at a high risk of being targeted (e.g., journalists, political figures), Google offers this program. It uses physical security keys and other advanced measures to provide the strongest level of account security.
- My Activity and Data & Privacy settings: Google collects a vast amount of data to personalize your experience. In your Google account settings, you have the power to view and delete your activity history (web, app, and location) and control what data is saved in the future.
Android’s Core Security Features.
- Google Play Protect: This is Android’s built-in malware scanner. It works in the background, continuously scanning your device for any potentially harmful apps from the Play Store. Ensure it is always enabled.
- Privacy Dashboard: Similar to iOS’s Privacy Report, the Android Privacy Dashboard gives you a visual breakdown of which apps have accessed your permissions in the last 24 hours. It’s an excellent tool for spotting apps with questionable behavior.Private Space (Android 15+): This feature creates a locked, separate section on your device that acts like a digital vault. Apps and data within this space are hidden from the main app menu, recent app lists, and notifications. This is perfect for keeping sensitive work or personal information completely separate and protected.
- Theft Protection (Android 15+): This new feature uses on-device AI to detect theft. If a thief tries to disconnect your phone from the internet or disable “Find My Device,” the device will automatically lock itself and require your PIN or password. This adds a crucial layer of security, even if your phone is taken offline.
Conclusion:
We’ve explored the digital world in your pocket, from the simple, foundational lock screen to the complex, nuanced settings within each platform. The journey from a vulnerable user to a vigilant guardian isn’t about becoming a cybersecurity expert; it’s about adopting a mindful and proactive approach to your digital life.
The key themes are clear:
- Foundational Security: A strong passcode and an enabled “Find My” feature are the non-negotiable first steps.
- Mindful App Management: Be critical of permissions, regularly review your privacy dashboard, and restrict what apps can see and do.
- Smart Connectivity: Be cautious with public Wi-Fi, turn off Bluetooth when not in use, and be a skeptic when faced with deceptive messages or calls.
- Platform-Specific Tools: Leverage the powerful, built-in security features of your iPhone or Android device, from 2FA to advanced data protection and Google’s security checkups.
Security isn’t a one-time task; it’s a continuous habit. Small, simple steps can make a monumental difference. Taking a few minutes to review your settings, to install an update, or to reconsider an app’s permissions can be the difference between a secure digital life and a compromised one. Your phone is a tool, and you are its master. By taking control of these settings, you are not only protecting your own data, but also your peace of mind.

FAQs
Q1: Will turning on all these settings slow down my phone or use more battery?
A1: Most of the security settings mentioned, such as a strong passcode, app permissions, and system updates, have a negligible impact on your phone’s performance or battery life. Features like iCloud Private Relay or a VPN can slightly increase battery consumption and might slow down your internet speed, as they route traffic through a secure server. However, the security benefits they provide far outweigh these minor inconveniences, especially on public networks.
Q2: What is a VPN, and do I really need one?
A2: A VPN (Virtual Private Network) creates an encrypted tunnel for your internet traffic. This makes your data unreadable to anyone trying to snoop on your activity, particularly on unsecure public Wi-Fi networks. You don’t necessarily need a VPN for your home network, but it is highly recommended if you frequently connect to public Wi-Fi at coffee shops, airports, or hotels to protect your personal information from hackers.
Q3: Is it safe to use biometrics like Face ID or fingerprint unlock?
A3: Yes, biometrics are generally very safe and are a superior alternative to a simple PIN or swipe pattern. They use advanced technology to create a unique digital map of your face or fingerprint, which is stored securely on your device. They are extremely difficult to spoof and provide a high level of convenience and security. Always ensure you also have a strong, complex passcode as a backup.
Q4: What should I do if my phone is lost or stolen?
A4: Immediately use your phone’s built-in “Find My” (iPhone) or “Find My Device” (Android) feature. Log in from another device and activate “Lost Mode” (iPhone) or “Secure Device” (Android). This will lock the phone, display a message, and track its location. If you are certain the phone cannot be recovered, use the “Erase Device” option to remotely wipe all your data, preventing a thief from accessing it.
Q5: Is Android or iPhone more secure?
A5: This is a complex and often debated topic. iPhones, with their closed ecosystem, are often considered more secure “out of the box” because Apple has strict control over hardware, software, and the App Store. Android’s open-source nature means it is more customizable but can be more vulnerable, especially on older devices or when users download apps from third-party sources. Both platforms have excellent built-in security features, but a user’s habits and settings are ultimately the most important factor.
Q6: I’ve heard about “jailbreaking” an iPhone or “rooting” an Android. Is that a good idea?
A6: No. “Jailbreaking” (iPhone) or “rooting” (Android) removes the security safeguards put in place by Apple and Google. It allows you to download apps from unvetted sources and customize your phone in ways the manufacturers don’t allow. While this may seem appealing for power users, it makes your device highly vulnerable to malware, viruses, and security exploits. For the vast majority of users, it is not worth the significant security risk.
Q7: How do I know if I have a virus on my phone?
A7: Unlike a computer, viruses on phones are less common due to the app sandboxing model. However, signs of malware can include: unusual battery drain, pop-up ads, apps crashing frequently, unexplained data usage, or your phone becoming excessively hot. If you notice these symptoms, first check your app list for any unfamiliar apps and delete them. You can also run a scan using a reputable mobile antivirus app from the official App Store or Play Store.
Q8: Is it safe to use my phone for online banking?
A8: Yes, it is generally safe, provided you take the proper precautions. Always use your bank’s official app (downloaded from the official app store) and never log in through a link sent in an email or text. Ensure you have a strong passcode and 2FA enabled on your bank account. Avoid using public Wi-Fi for banking transactions; if you must, use a VPN.
Q9: Can someone spy on me through my camera or microphone?
A9: It is possible for a malicious app to do so if you have granted it permission. Both iOS and Android now provide on-screen indicators (a green or orange dot/light) to alert you when your camera or microphone is in use. If you see this indicator when you’re not actively using an app that needs it, immediately go to your privacy settings and revoke that app’s access. This is why being mindful of app permissions is so crucial.
Q10: How often should I change my passwords?
A10: While a general rule of thumb used to be every 90 days, security experts now recommend focusing on using a strong, unique password for every account and using a password manager to store them. You only need to change a password if you suspect it has been compromised (e.g., a data breach), or if the account doesn’t support 2FA. For your most critical accounts (email, banking), 2FA is far more important than frequent password changes.